ML and AI play a crucial role in cybersecurity
We are living in an advanced digital world where computerized digital system forms the backbone of our everyday lives, cyber-attacks are regularly focusing on the computerized environment and ruins everything each business, individual, even government association. In 2020, more than 1.5 billion online records were undermined intellectual data due to hacking and different kinds of cyber-attacks.
Day-by-Day cyber attacks are continuously growing with high speed and crypto-jacking, spam & phishing, data breaches, mobile malware, IoT attacks, and ransomware make it more sophisticated. A cyber attack can damage the reputation of an organization by attacking an organization's data.
Network security is more vital than ever. The most consequential algorithms are Machine Learning (ML) and Artificial Intelligence (AI) can fight against all cyber attacks with all possible weapons.
What is artificial intelligence?
AI is a wide-ranging branch of computer science concerned with building an intelligence machine with the ability of a computer or computer-controlled robot to perform tasks using real-time data and human intelligence.
AI can efficiently analyze user behaviors, deduce a pattern, and identify all forms of abnormalities or irregularities within the network. With such data, it's much easier to identify cyber vulnerabilities quickly.
Artificial intelligence software will provide you with the ability to process a near-limitless volume of threat data and to effectively prevent and reply to hacks and breaches within the world of today’s deadly cybersecurity.
What is machine learning?
Machine learning, a formal branch of AI and computational learning theory builds systems that learn directly from the data that is fed to them and effectively program themselves to make predictions. Machine learning more influential for preventing cyber attacks.
All machine learning algorithms in cybersecurity are grouped into unsupervised learning or supervised learning algorithms. Supervised learning algorithms always require a database which is in the form of a labeled training database. So, supervised learning algorithms are not used to detect cyber attacks. Unsupervised learning algorithms are well suited for detecting cyber-attacks or suspicious activity because unsupervised learning algorithms do not require a labeled training database.
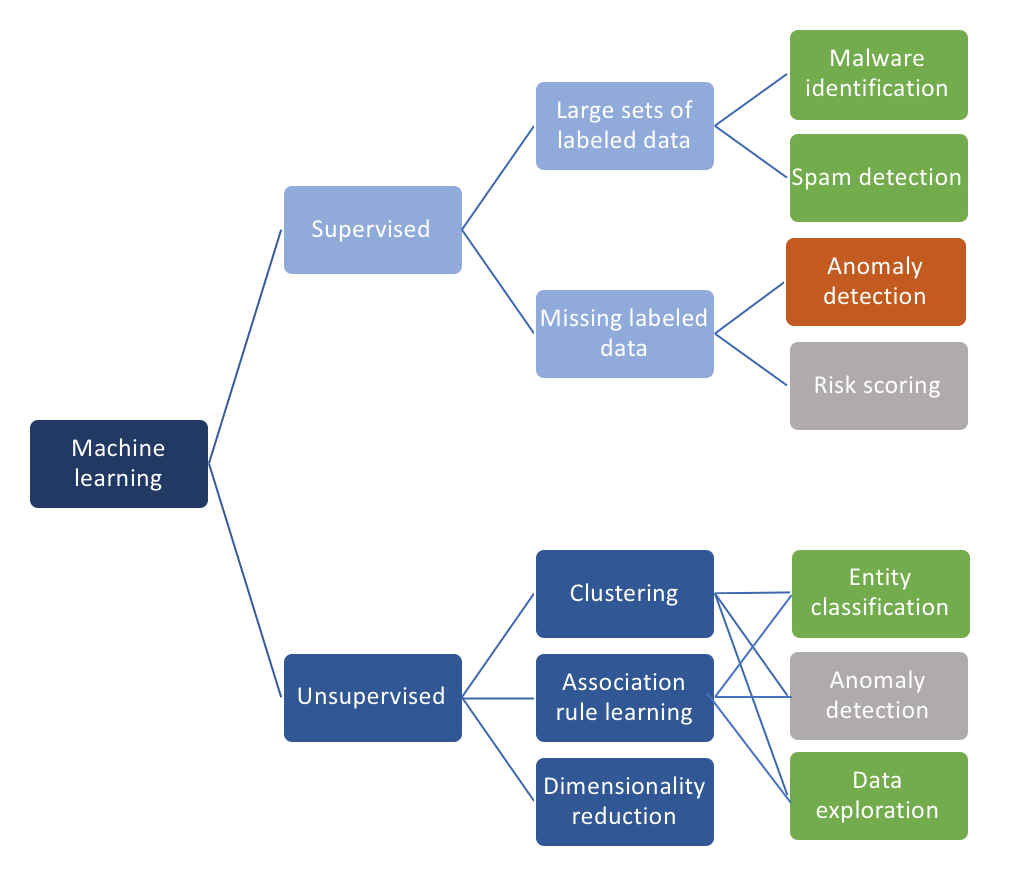
What’s the real role of AI and ML in cybersecurity
AI and ML can change the face of cybersecurity.
As an advance in AI and ML move at back neck speed, the use of AI and ML is expected to grow at a heartening pace in cyber defense and will add tremendous intelligence and power to fight against cyber attacks.
Artificial intelligence and machine learning in cybersecurity are used to learning how to remove noise or unwanted data and to enable security experts to understand the cyber environment in order to detect abnormal activity. AI and ML provide details on potential incidents using anomaly detection and clustering.
Machine learning in cybersecurity systems can analyze patterns and learn from them to help prevent similar attacks and respond to changing behavior. It can help cybersecurity teams be more proactive in preventing threats and responding to active attacks in real-time. It can reduce the amount of time spent on routine tasks and enable organizations to use their resources more strategically.
The machine learning algorithm can easily load big data as compared to others and the ML algorithm continuously monitoring all network activities. ML is not a 'plug & play' techniques it requires some human experts for detecting the real attacks from all suspicious activities.
According to google trends, AI and ML have shown a steady increase in interest since 2015.
Open-source machine learning and data science tools such as the python sci-kit package are freely available, very powerful, and often used to build security tools.
Early attempts of machine learning at cybersecurity haven’t met much success when compared with machine learning in other fields. Recently, some major companies have acquired machine learning capabilities. This includes Sophos acquiring Invincia, Hewlett-Packard buying Niara, and Radware buying Seculert. This is an indication that some of the major organizations see machine learning as a big asset to cybersecurity, in the future.
Machine learning regularly improves its algorithm in cybersecurity. Recently ML include MIT's and Computer Science and AI Laboratory to form PatternEx.
AI allows cybersecurity teams to make powerful human-machine partnerships that push the boundaries of our knowledge, enrich our lives, and drive cybersecurity in a way that seems greater than the sum of its parts.
Use cases of AI and ML in cybersecurity
Detection of sophisticated cyber-attacks and attacks prevention
Machine learning algorithms will help businesses to find malicious activity faster and prevent attacks before they occurred.
Each organization looking for an innovative cybersecurity technology to strengthen its overall cyber defense strategy and protect the company’s critical assets, including intellectual property and sensitive client data from sophisticated cyber-attacks. Machine learning can analyze the behaviors of each and every device, user, and network to learn the specific patterns, and identify any anomalous behavior, and alerts the organization before real damage is done.
Analyze mobile endpoints
AI and ML algorithm establishing the behavior for the endpoint through a repeated training process. If something out of the ordinary occurs, Algorithm can flag it and take action — whether that’s sending a notification to a technician or even reverting to a safe state after a ransomware attack.
Google is using AI to analyze mobile endpoint threats, while enterprise is seeing an opportunity to protect the growing number of personal mobile devices.
Some of the vendors are announcing their mobile solution. Zimperium, LookOut, Skycure (which has been acquired by Symantec), and Wandera are seen to be the leaders in the mobile threat detection and defense market. Each uses its own machine learning algorithm to detect potential threats.
AI-based threat mitigation
The AI-powered system will be an integral part of the cybersecurity solutions. It will also be used by criminals to harm organizations. Most of the organization train their machine-learning algorithm to recognize attacks created by other machine learning algorithm, and protect their own organization by phishing, spyware, or distributed denial-of-service attacks.
Network threat analysis
Nowadays more companies are digitizing their operation and update their network to an internal hybrid network. These vast networks require extensive network security resources to manage their all activities, communications, transactions, connections, and policies.
ML-based network security software continuously monitors all network activities, incoming and outgoing signals to identify any suspicious activity in the network data.
Automate repetitive security tasks
Machine learning can rapidly analyze, curate, visualize the potential actions, and handle the low-risk alerts or repetitive work and tactical firefighting like interrupting ransomware in order to free up analysts for higher-value or strategic decision-making task.
Cybersecurity and it's Future with ML and AI
All organizations are conscious of how cyber-attacks have impacted their organization's reputation. To protect from cyber attacks many organizations use multiple ways to protect and build a complete machine learning algorithm shield to defend the cyber attacks. First of all, each security system uses the best suitable firewall for controlling and filtering network traffic. The second line of defense consist of antivirus software. These tools scan through the system to find and eliminate malicious code and files.
With these two lines of defense organizations regularly run backups as a part of disaster recovery plans.
Top Recommended Freelancers
More than 1,000,000 freelancers ready to tackle any kind of project

Tsitsi Hazel S.
$22 /hr, Zimbabwe
Ajay N.
$9 /hr, India
Adia A.
$25 /hr, Finland
Charles C.
$22 /hr, Nigeria
Tina L.
$100 /hr, Nigeria
Luckman M.
$19 /hr, South Africa
Ashokkumar Gnan N.
$24 /hr, India
Supradha A.
$30 /hr, India![Sampat Cyber Security Analyst and Consultant [CEH]](/assets/thumbnails/19/1926b3fbfd115e193f50c001be8139fc.jpg)
Sampat
$5 /hr, India
Diko M.
$11 /hr, India
Francisoloo O.
$45 /hr, Kenya
Harika R.
$2 /hr, India

